A virus has been distributed worldwide that affects the router devices that provide us with Internet connection at home and in offices. According to the FBI, it is a cyber-attack from Russian hackers that would have affected more than 500,000 devices of this type spread around the world.

The scope has been so extraordinary that the FBI itself has disseminated worldwide recommendations that all those potentially affected should do. It does not affect all brands and models and apparently, the objective of this attack has already been neutralized. It no longer represents an imminent danger, however, they recommend that we perform a factory reset on the possibly affected models.
What does it consist of?
The malware that has been distributed worldwide is known as VPNFilter. It seems to have exploited some vulnerability of certain devices and the use of weak passwords.
The aim of the attackers was to form a network of bots to carry out coordinated mass attacks, and even leave them unused. Although the FBI took control of this botnet by closing a website that was to coordinate remote attacks, many routers were infected. The warning from the US Government aims to clean those devices.
The malicious capability of VPNFilter is important, because if activated it can damage the affected devices themselves. It would also allow to inspect traffic, steal files and potentially enter the network to which these devices are connected.
Devices in up to 54 different countries appear to have been affected, and the information is suspected to have been directed from Russia.
What devices does it affect?
These are the models of WiFi routers vulnerable to VPNFilter that are known, but there could be more:
- Linksys E1200
- Linksys E2500
- Linksys WRVS4400N
- Mikrotik RouterOS for Cloud Core Routers: Versions 1016, 1036, y 1072
- Netgear DGN2200
- Netgear R6400
- Netgear R7000
- Netgear R8000
- Netgear WNR1000
- Netgear WNR2000
- QNAP TS251
- QNAP TS439 Pro
- QNAP NAS devices running QTS software
- TP-Link R600VPN
What should we do?
The instructions issued by the FBI worldwide may have been misinterpreted by some media. The first news asked users to “reboot” the router, alluding to the possibility of simply turning it off and on again.
But this error is due to a mistranslation of the term “reboot” which in English means restart, but in this context what it indicates is that we must restore the device to the factory state.
If your home or business router is one of the ones listed above, the recommendation is to reset it to factory default or simply reset it.
To do this, use the micro push-button that all of them usually present on the back with the “reset” or “restore” indicator. It is usually a small micro-perforation that must be activated with a very fine tip, such as that of a clip or pin.
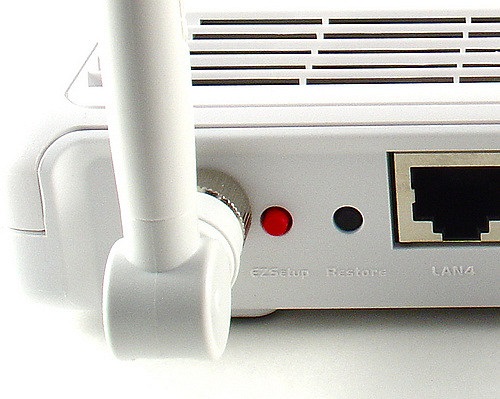
It is usually necessary to keep it pressed for a few seconds until you see a change in the indicator lights. After a short period of time, the router will return to the factory default settings.
Remember that, for our security, we must at least change the WiFi access password to a different one than the one set at the factory. We will choose a new long and complicated password, of the safest possible type or WPA2, to prevent others from guessing it in a possible cyber-attack.
Remember that in addition to removing any malware that may have infected us, other settings that we may have saved will also be deleted, such as open ports for P2P programs (Emule for example), MAC filtering, blocked URLs, connection-limiting times, etc.
