Windows 7 stops receiving updates today, so it will be more vulnerable to cyber-attacks. Here’s what to do if you’re still using it.
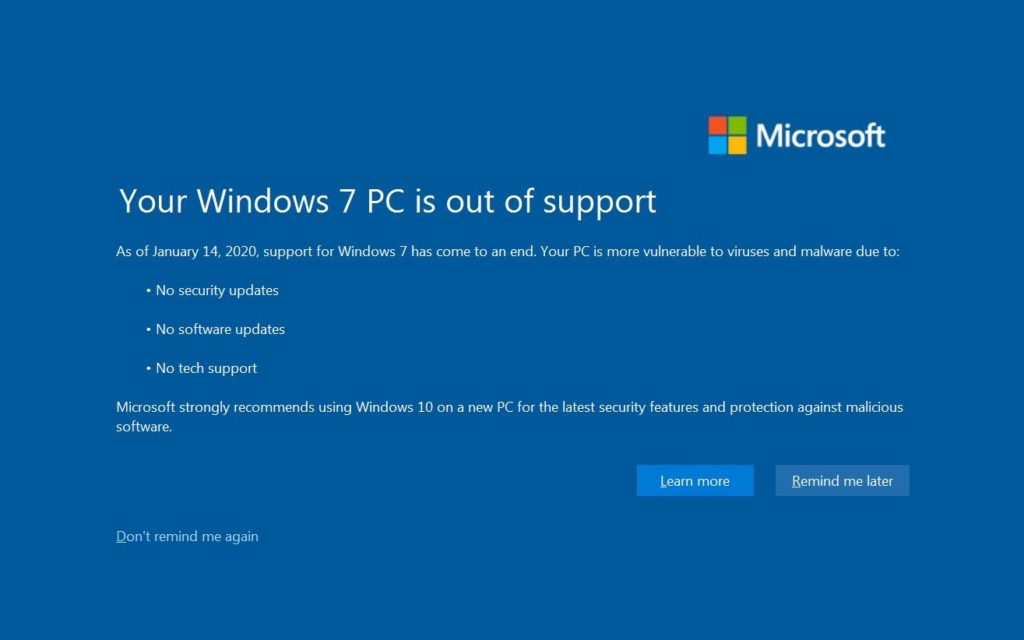
As of January 14, 2020, the Windows 7 operating system stops receiving updates, which means that security holes discovered from now on will not be patched.
In this way, cybercriminals will find this operating system a target for their attacks. According to Net MarketShare figures, Windows 7 is still the second most used version on computers today (32.74%), only behind Windows 10 (47.65%) and even surpassing MAC and Linux.
Users who still use Windows 7 on their computers should consider upgrading to the latest version of Microsoft. Since it will be the only way to remain protected against the types of malware that use security holes to sneak into devices.
LEER MÁS